Top Six Things to Consider with an Identity-as-a-Service (IDaaS) Solution – Conclusion
 An IDaaS solution can prove to be a tremendous time saver, improve user satisfaction and IT productivity and addresses many of the shortcomings associated with password sprawl. When considering an IDaaS solution, partner with a vendor that can deliver on all of the top IDaaS considerations discussed in this paper and select an IDaaS solution that can centrally authenticate users with their Active Directory identity without replicating to the cloud, that unifies mobile and app access management, is ready for your enterprise globally and one which gives IT valuable insight into which applications and how devices are used and when — restoring lost visibility and control. In doing so you will reap many important benefits including:
An IDaaS solution can prove to be a tremendous time saver, improve user satisfaction and IT productivity and addresses many of the shortcomings associated with password sprawl. When considering an IDaaS solution, partner with a vendor that can deliver on all of the top IDaaS considerations discussed in this paper and select an IDaaS solution that can centrally authenticate users with their Active Directory identity without replicating to the cloud, that unifies mobile and app access management, is ready for your enterprise globally and one which gives IT valuable insight into which applications and how devices are used and when — restoring lost visibility and control. In doing so you will reap many important benefits including:

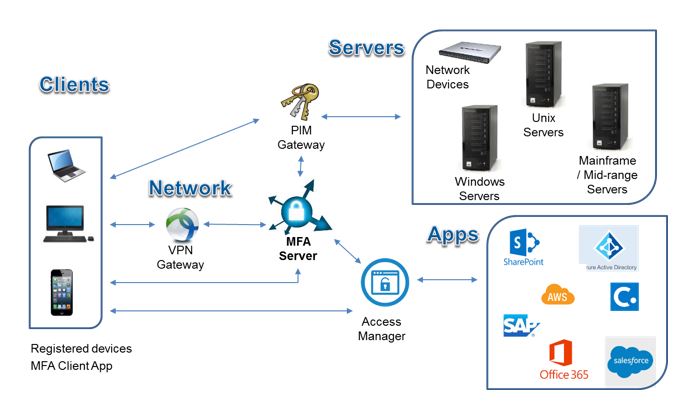
Centrify uniquely unifies cloud app and mobile engagement.
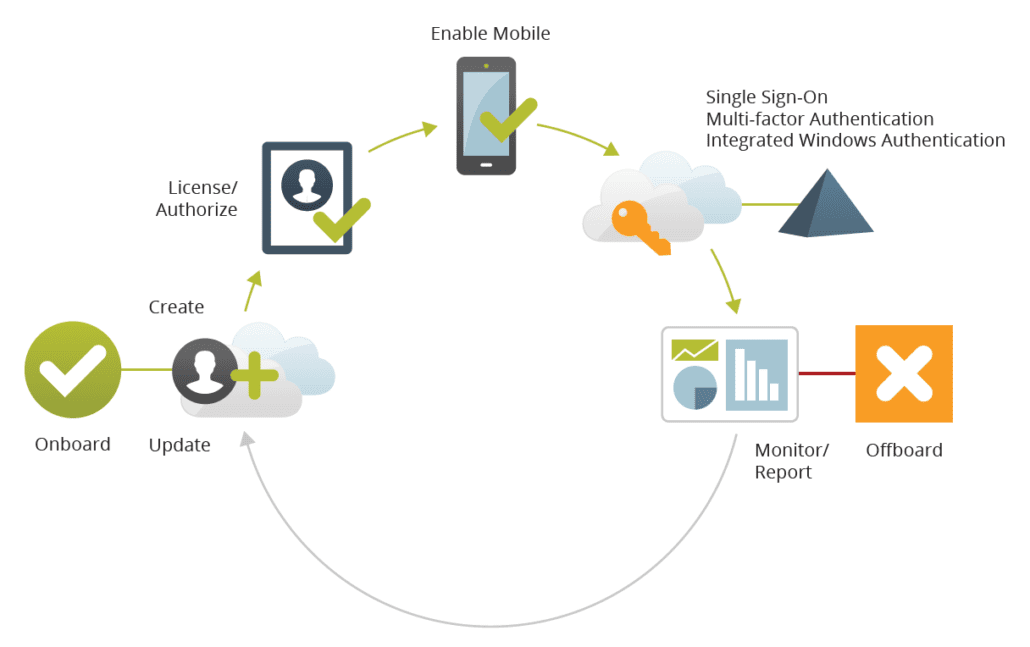
- Improved user productivity and satisfaction: Make users productive day one without extensive manual checklists and time consuming helpdesk calls. Reduce the number of times a user has to remember and self-manage passwords, and make it easier to self-service access to all of their apps, devices and identity.
- Reduced helpdesk costs: Return value in improved productivity and as much as a 95% reduction in app account and password reset calls.
- Lower app lifecycle costs: Through turnkey provisioning for apps and by tightly integrating with Active Directory the delivery of app single sign-on and mobile security is more cost efficient because IT uses existing technology, skillsets and processes that are already in place.
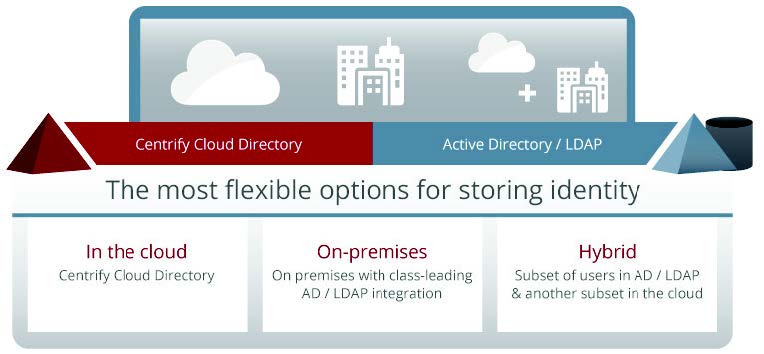
- Improved security: IT can remove users’ access to all business-owned cloud and on-premises applications by simply disabling their Active Directory account, which is already a common practice at the time an employee leaves the company. And unlike other solutions, it does not duplicate your existing identity data into the cloud and out of your control — it remains secure inside your corporation.
- Reduced compliance costs: IT can remove users’ access to all business-owned cloud and on-premises applications by simply disabling their Active Directory account, which is already a common practice at the time an employee leaves the company. And unlike other solutions, it does not duplicate your existing identity data into the cloud and out of your control — it remains secure inside your corporation.