IGA Efficiencies for Large Enterprises
What do Henry Ford and Enterprise Identity Access Management programs have in common?
By Keith Squires, PathMaker Group President & CEO

Is this your team?
-
tired
-
tapped out
-
overworked
-
behind
-
understaffed
-
not producing efficiently
-
maybe even ready to quit
It may be time to think about a factory approach to implementing Identity and Access Management.
Once an organization successfully implements foundational IGA capabilities, stakeholders will begin to realize key benefits –- efficient access governance processes, faster access setup for employees, automated event triggers, easier audit reporting. It won’t be long before requests from these impacted groups begin to overwhelm your already busy security admin team.
Now begins a new challenge – how do we support this increasing pace and volume of support requests. Application owners want ALL their apps under IGA governance, departments with high employee turnover need ALL their apps and roles available for self-service access request, IT teams want all these one-off application setup processes off their plate. As the access, compliance and audit world gets easier to manage, word gets around.
So what can security admin do to face these increasing workload challenges head on and still manage the day to day operations with acceptable SLAs?
Well if you ask Henry, it’s all about the process!

Simplicity, consistency, uniformity produces efficiency, speed, quality and hopefully stronger security!
With many of our clients, we’ve helped them establish an approach we call FactoryPathtm, which leverages years of experience and process improvement to provide valuable guidance, templates, and processes for deploying high volumes of IGA artifacts like application integration, roles, and other high volumes of configuration objects.
The key concept is to take a step back, briefly, and think not just about getting through the work, but the approach to doing the work. Yes, there’s pressure to deliver, but we have to do this long-term, so let’s work on gaining some efficiencies along the way!
Let’s take application integration as the first example:
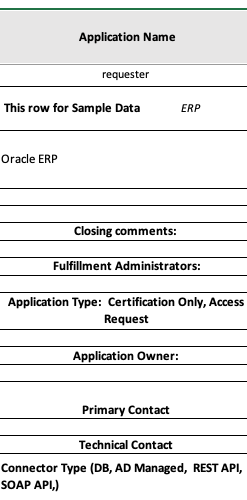
To build a repeatable process, Inputs or prerequisites have to be patterned and consistent.
Let’s think in terms of having a form that you can circulate to your application owners. “Fill this out, and then let’s talk”. Until your app owners can supply the minimum required data points, let’s not waste time talking about this application. See there! You just saved yourself 30 – 60 minutes of pointless emails, calls and meetings and all you had to say was “please start by filling out this form”.
What goes on the form? It depends . . . Every organization will approach this process in a slightly different manner, but the basic metadata should be the same:
-
Application owner
-
Technical contact
-
Security model (groups, roles, menu options, etc.)
-
Access approver
And you need to know setup and account modification process steps:
-
How do you setup a new account
-
How do you grant access to a new account
-
How do you remove access from an account
-
How do you disable an account
-
Will you delete a disabled account? If yes, after how long?
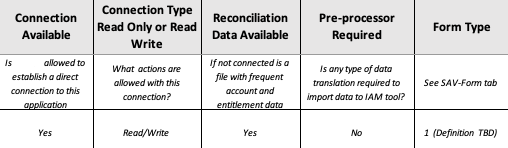
AND NOW FOR THE TECHNICAL DETAIL:
-
 How do we connect to this application?
How do we connect to this application? -
Can our IAM system aggregate in all the accounts, entitlements, groups, roles, etc. via API or WAS calls?
-
If we have to read from an extract file, who will provide this file, and how often?
-
Application owner
-
Technical contact
-
Security model (groups, roles, menu options, etc.)
-
Access approver
And you need to know setup and account modification process steps:
-
How do you setup a new account
-
How do you grant access to a new account
-
How do you remove access from an account
-
How do you disable an account
-
Will you delete a disabled account? If yes, after how long?
And now for the technical detail:
-
How do we connect to this application?
-
Can our IAM system aggregate in all the accounts, entitlements, groups, roles, etc. via API or WAS calls?
-
If we have to read from an extract file, who will provide this file, and how often?
This is just a sample of the topics, questions, information that has to be gathered, analyzed, reviewed, approved.
This is not a trivial or quick process. It takes focused attention and dedication to move through the 100s of applications in a typical larger enterprise.
The bottom line is that companies that gain significant traction build and manage a process that enables efficiency through consistency and repeatability. We’ve seen this model executed successfully with many of our clients. I know your teams may be tired, but you can do this! Take a step back, focus on the process, and hopefully you can gain real efficiencies to make great progress.

 How do we connect to this application?
How do we connect to this application?