Addressing NIST’s New Risk Management Framework
The National Institute of Standards and Technology (NIST) created a series of publications that provide guidance for federal agencies on the implementation, certification and accreditation of federal information system security. The same guidelines hold true for all commercial agencies/companies as well.
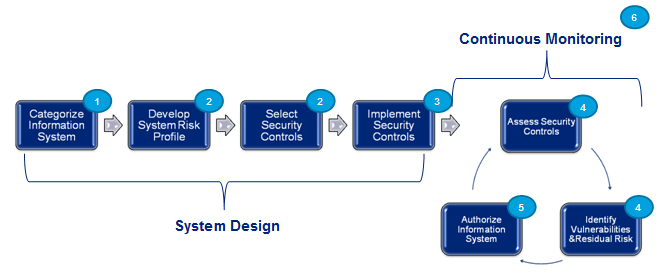
So the question that comes to our mind What is NIST’s New Risk Management Framework? NIST describes the RMF model as a series of six repeating steps designed to identify the security mechanisms necessary for an IT system, implement those protections, and validate their proper operation over the systems lifecycle.