5 Things to Consider with Multi-Factor Authentication
Chris Fields, VP of Security Strategy

Multi-factor authentication (MFA) is becoming a mandatory component of a secure identity and access management landscape. You know you need to implement MFA and are contemplating where to start and what other considerations need to be evaluated. Below are 5 things to consider on your MFA journey that will 1) save you time, 2) prevent rework and 3) avoid frustrating end users:
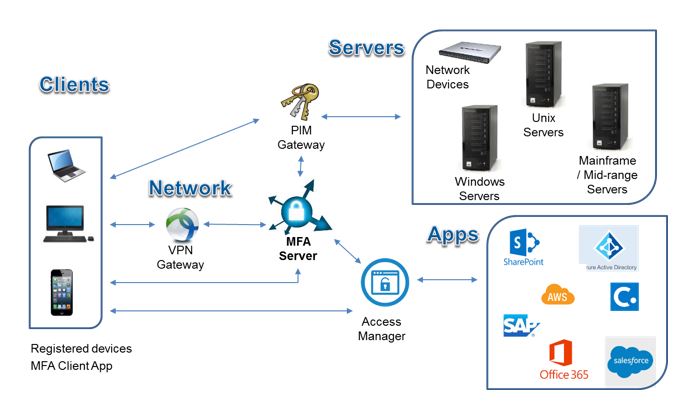
1. MFA Server
The MFA server is the “brain” that drives all policy decisions and functionality. Think of it as the horse you choose to ride on your journey to the MFA finish line. Flexibility to provide multi-factor (something you know, have or are), risk-based, step-up or other advanced access capabilities are key. This “brain” should have broad out of the box integrations to various endpoints to maximize use of its capabilities in all facets of your identity and access management landscape. The MFA Server should be accessible to your on-premise and cloud applications, services and servers. The placement and mix of those endpoints may even determine whether you select an on-premise or cloud MFA server.
2. MFA Clients
The MFA clients are the various devices that end users use to interact with the MFA server for proper authentication vetting. A capable MFA server will support myriad MFA client devices and identification techniques including desktops, laptops, tablets, mobile phones, grid cards, smart cards, RFID cards, key fobs (OTP), hard tokens (OTP), soft tokens (OTP) and biometric readers (to name a few). Mobile phones are becoming a very popular option because they not only are ubiquitous but also support many of the identification techniques that normally require deployment of additional hardware, especially one-time password (OTP) & biometric options. Be sure to confirm support for all the client devices that are most common in your organization to minimize challenges with leveraging your MFA server before you make your selection. Also, make sure you select the right identification techniques based on your user populations and factor in the deployment time and complexity.
3. VPN Integration
Remote access is typically the first use case out of the gate for MFA integration. Most companies already have a VPN gateway in place so it becomes the first “stake in the ground” for making your MFA server decision. Ideally you would pick your MFA server first, to maximize the capabilities I described in the MFA Server and MFA Client considerations, but reality isn’t always so neat and clean. You may be lucky to have had your VPN software long enough to be at an inflection point, where the current technology is due for an upgrade or replacement and it makes sense to re-prioritize your VPN selection based on your MFA selection. This is where going with a capable MFA Server yields the benefit of a wide range of out of the box integrations with popular VPN platforms.
4. PIM Integration
Privileged Identity Management (PIM) integration is typically the next integration point for MFA. VPN integration ensures that the user and device are vetted properly to connect to the network remotely, but once on the network, both internal users and external users need to strengthen their authentication to servers for privileged access. Instead of integrating each server individually with your MFA solution, integrating through a Privileged Identity Management gateway is becoming a more popular alternative. Similar to the VPN integration scenario, ideally you would select your MFA solution first and maximize integration options with popular PIM solutions.
5. Access Management Integration
Application Access Management integration is usually the next integration point for MFA. Having an access management solution in place is a best practice for managing access to applications, especially web applications. Integrating your MFA solution with an access management solution provides an efficient mechanism for providing MFA capabilities at the individual application level. Since access management solutions form the authentication and authorization backbone for internal and external applications, this essentially extends your MFA capability to internal and external users in a very efficient manner.
Conclusion
Taking these 5 considerations into account when you are looking at your MFA solution will lead to a much less bumpy road for your administrators and end users. The end result will be a consistent MFA end user experience for your users across the enterprise and a sound technical approach to solving the most common MFA use cases.
