Solution Brief: Threat & Response Expertise
/in Threat Advisories, Threat Management, Uncategorized/by Howard Mahoney Qualified security staff are hard to find and difficult to retain. And, operating a dedicated 24/7 security operations center (SOC) can be expensive. Plus, a mix of security tools makes it nearly impossible to understand attack data holistically, requires expensive and difficult-tofind skilled resources, and requires substantial effort to get to value.
Qualified security staff are hard to find and difficult to retain. And, operating a dedicated 24/7 security operations center (SOC) can be expensive. Plus, a mix of security tools makes it nearly impossible to understand attack data holistically, requires expensive and difficult-tofind skilled resources, and requires substantial effort to get to value.
As a result, security and IT directors spend far too much time and money on breach prevention and threat detection, and it takes significant efforts, filter through the noise, chase down false positives and focus on actual attack data.
With over 82% of breaches1 caused by malware, user misuse, or social attacks, there must be a better way.
With nearly two decades of experience providing Security Operations to thousands of organizations Alert Logic has been built to ensure these demands can be met by our customers without the expense of building and maintaining their own teams or needing to source security detection technologies from multiple third parties.
Thycotic – Company Overview
/in Uncategorized/by Howard Mahoney Why Choose Thycotic
Why Choose Thycotic
Stay Ahead Of Attackers. Prepare For Audits. Protect What Matters Most.
Thycotic empowers more than 10,000 organizations around the globe, from small businesses
to the Fortune 500, to manage privileged access. We make enterprise-grade privilege
management accessible for everyone by eliminating the need for complex security tools and
prioritizing productivity, flexibility and control. You’ll achieve more with Thycotic than with any other
privilege security tool.
Thycotic Company Overview and Fact Sheet
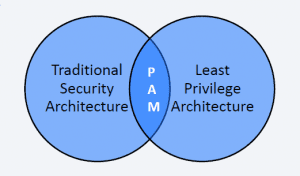
Secret Server – Privileged Account Management At Enterprise Scale
/in Uncategorized/by Howard MahoneyDiscover, manage, protect, and audit privileged account access across your organization.
As cyber threats continue to increase in volume and sophistication, effective and agile Privileged Account Management (PAM) has become mission-critical for organizations of every size. Now you can adopt an aggressive privileged account security posture with Secret Server, the only fully featured PAM solution available both on premise and in the cloud. Empower your security and IT ops teams to secure and manage all types of privileged accounts quickly and easily.
Bringing Identity to Enterprises of All Sizes
/in Identity Management, SailPoint, Uncategorized/by Howard Mahoney
There is a massive transformation happening across the globe as every business leverages the power of technology to keep themselves competitive.
This digital transformation has had vast implications to the speed of business, but it has also made managing users and resources significantly more complex. Modern business environments are more open and interconnected than ever before. Employees, contractors, suppliers and business partners need to access company resources from a variety of devices and locations.
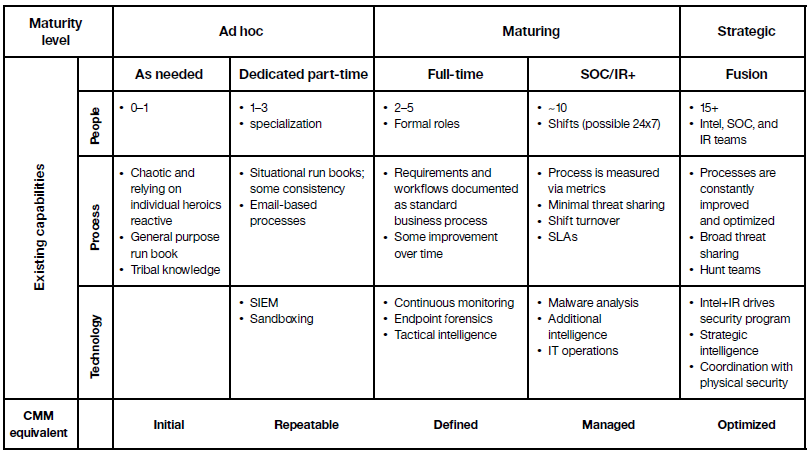
IBM Security – Six Steps For Building A Robust Incident Response Function
/in Uncategorized/by Howard MahoneyThis is the decade of incident response.
Organizations globally realize that working only to prevent and detect cyberattacks will not protect them against cyber security threats. That is why IBM Resilient® was developed: to arm security teams with a platform for managing, coordinating, and streamlining incident response (IR) processes.
IBM Security has had the privilege of working with organizations of all sizes and across all industries as they implement Resilient solutions to develop more sophisticated and robust incident response functions. These organizations build IR processes that are consistent, repeatable, and measurable, rather than ad hoc. They make communication, coordination, and collaboration an organization-wide priority. They leverage technology that empowers the response team to do their job faster and more accurately.
Creating an Identity-aware Organization from Infrastructure to Users
/in Uncategorized/by Howard MahoneyIBM Whitepaper – Learn the Factors that Increase Cost and Risks in a Hybrid IT Environment
/in Uncategorized/by Howard MahoneyDownload your IBM whitepaper IBM_Optimized Sourcing in Hybrid IT Environments
Who We Are
PathMaker Group is a specialized Security and Identity Management Consultancy, blending core technical and product expertise, consultative know-how, and extensive implementation experience.
Pathmaker Group
DALLAS-FORT WORTH
635 Fritz Drive
Suite 110
Coppell, TX 75019
(817) 704-3644
info@pathmaker-group.com