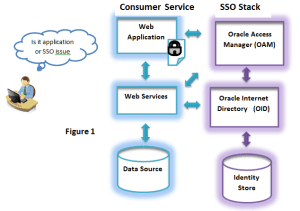
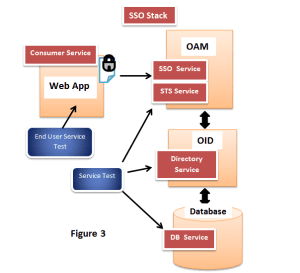
Building an IAM Roadmap – A five step process
Since 2003, our teams have been part of over 350 efforts to implement or rescue Identity and Access Management (“IAM”) projects. Our customers, most of whom have become great friends, are from all over the US, crossing many disparate and unique industries. In most cases, they are working to solve similar business problems and to fix or improve the same processes.
On many occasions, we started from the ground floor and had the opportunity to create a roadmap for their long-term strategy. To those familiar with IAM capabilities, it may seem obvious what to prioritize and where to start, but let’s not be so quick to jump to what looks like an easy decision. All IAM capabilities are not created equal.
Our job as a systems integrator is to successfully implement these complex IAM security technologies, and to ensure that our customers maximize the return on their significant IT investments. As we help guide our customers through these decisions, this ROI is always our priority, which leads us to the topic for today.
So how, exactly, can we accomplish this? This article is all about alignment. Having alignment between IT and the other key stakeholders will significantly reduce the risk of your IAM projects failing and losing or wasting precious budget dollars.
How can you ensure you have correct alignment? Here’s how our IAM Roadmap process breaks down.
Step 1 – We start by prioritizing a list of over 100 key IAM capabilities. This list was compiled from our work over the years and is vendor agnostic. After a brief explanation to help educate the stakeholders, we apply a ranking of low, medium or high based on their opinion on how important the organization needs a certain capability. Typical examples of high priority capabilities are automated provisioning of accounts, self-service password reset and role recertification.
Here’s a common example of the final output
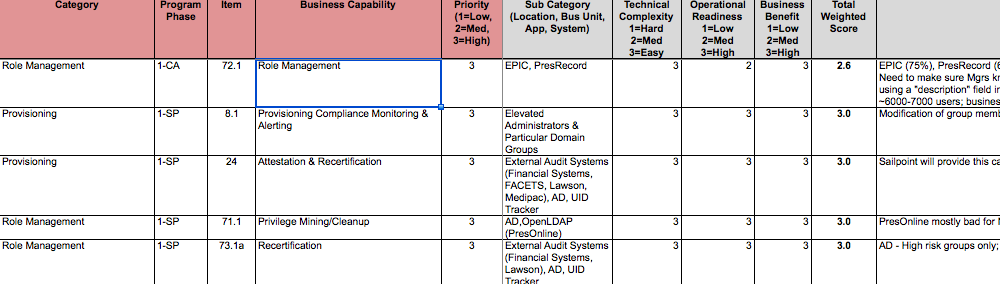
Step 2 – Once you have a high priority list to work from, we dig a little deeper into three categories of analysis. The first category is Business Benefit – How significant is the true Business Benefit of this capability? Is this just a shiny new IT toy or will the stakeholders see lift and leverage from adopting this functionality. It’s critical to have your business stakeholders at the table so they can weigh in.
Step 3 – The second category is for your technical staff regarding Technical Complexity – How technically difficult will it be to configure or customize this solution? Are there products that provide this feature and function out of the box? Will your team be able to update and maintain the tools going forward or is this going to be way outside of their comfort zone and expertise? Is it cost prohibitive based on the benefit? This is where we can weigh in to help provide some context as well.
Step 4 – The third and last category is about Organizational Readiness – can the company readily adopt the capability? Are there so many competing priorities that gaining mindshare and focus will be difficult? Do you have the buy-in from stakeholder leadership? Is everyone at the table truly on board with this project and these priorities? Will they drive the effort through their organizations?
Step 5 – Once you’ve made it through this list and conducted a robust debate and Q&A with these three key questions, it’s time to score and rank the results. Amazingly you will see a handful of capabilities that float to the top where the Business Benefit is high, the Technical Complexity is low and the Organizational Readiness is high. After a short review of the results with some discussion and debate, a solid scope of high priority capabilities emerge as candidates for the first one or two phases of a successful program.
The next step is to choose a product that can fulfill these priorities, and then you are off and running. The advantage you have is that your stakeholders are more educated and have bought into the process and priorities – they are aligned. At the first sign of deviating from scope or questioning why we are including specific capabilities, you simply go back to the prior analysis and remind the team of the decision-making rationale.
Does this IAM Roadmap process guarantee a successful project or program? Not necessarily. But having all your stakeholders at the table and aligned provides a huge advantage and a great start.