Directory Object Search
Have you ever wanted to perform an LDAP search in a workflow to check for … well let’s just say a duplicate UNIX UID.
In this example the account add workflow is checking to make sure the Unix UID is not in use by another account. The requirements in this instance are that UNIX UID can only be used once in a service. Once the duplicate is found the next step is up to you but in this case the account add was rejected.
First thing you have to do is expose the dataservices model. Add the following line to scriptframework.properties.
ITIM.java.access.dataservices=com.ibm.itim.dataservices.model.*
Example Script in Workflow Script Node:
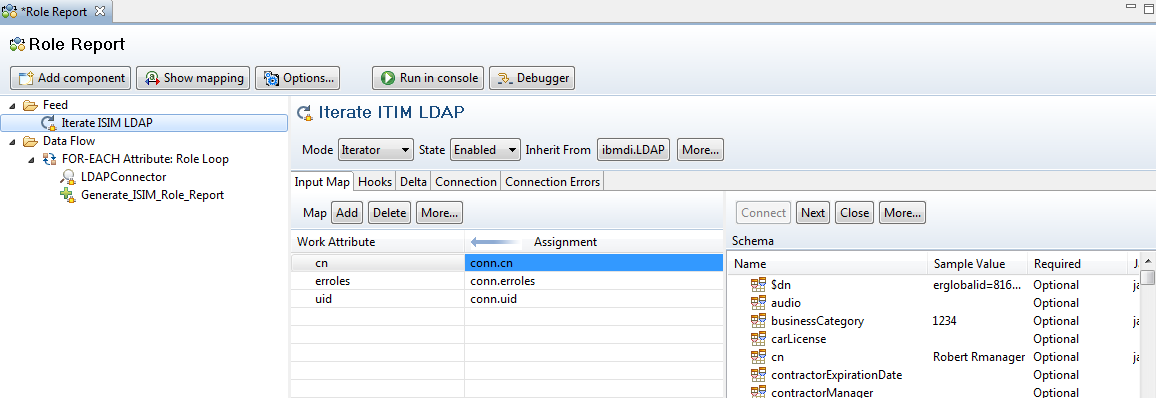
This script node is from an Account Add workflow. The script gets the service DN and erposixuid from the new account. The service DN and UNIX UID are used to verify the UNIX UID has not been used before in the same service. The Directory Object Search will search ITIM’s LDAP as you can see from the search base. There are also a couple examples to get the account attributes.
/* Search the current service for an account with the same unix uid */
var myAccount = account.get();
var myPerson = owner.get();
var unixUidMatch = ‘false’;
var dupAccountList = ”;
errorInd.set(‘false’);
/* Get Service DN */
var myServiceDN = myAccount.getProperty(“erservice”)[0];
var myInputPosixUid = myAccount.getProperty(“erposixuid”);
if (myInputPosixUid != null && myInputPosixUid.length > 0)
myInputPosixUid = myInputPosixUid[0];
else
myInputPosixUid = “unknown”;
if (myInputPosixUid != “unknown”) {
/* Search Accounts within Service for unix UID */
var searchFilter = ‘(&(erservice=’ + myServiceDN + ‘)(erposixuid=’ + myInputPosixUid + ‘))’;
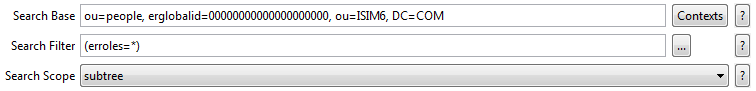
var searchBase = ‘ou=accounts,erglobalid=00000000000000000000,ou=XXX,O=XXX’;
var base = new com.ibm.itim.dataservices.model.DistinguishedName(searchBase);
var params = new com.ibm.itim.dataservices.model.SearchParameters();
var search = new com.ibm.itim.dataservices.model.DirectoryObjectSearch();
var results = search.fetch(base, searchFilter, params).iterator();
while (results.hasNext()) {
/* Duplicate Unix UID Found */
var dirObj = results.next().getDirectoryObject();
/* Get Account Object */
var mySearchAccount = new Account(dirObj.getDistinguishedName().toString());
var mySearchEruid = mySearchAccount.getProperty(‘eruid’);
if (mySearchEruid != null && mySearchEruid.length > 0) {
mySearchEruid = mySearchEruid[0];
if (unixUidMatch == ‘true’)
dupAccountList = dupAccountList + ‘ ,’+ mySearchEruid;
else
dupAccountList = mySearchEruid;
}
unixUidMatch = ‘true’;
}
OR
while (results.hasNext()) {
var dirObj = results.next().getDirectoryObject();
var myDupAccountID = dirObj.getAttribute(“eruid”);
if (myDupAccountID!=null) {
myDupAccountID = myDupAccountID.getValueString();
}
}




 About Ravi Srinivasan:
About Ravi Srinivasan: