3 Benefits of Abstracting Web-Based API with a Dedicated Gateway Layer
Right now, the solution du jour in the IAM space seems to be focused around enabling mobile and cloud based services for the enterprise. Organizations’ IT departments around the world are being tasked with providing the business with services to allow access and visibility of services to more platforms and providers than have ever been previously required. Mobile platforms, BYOD and SaaS provider requirements , along with new classes of threats against web based API’s, have given rise to the need to secure these services to in order to protect the organization from new security risks.
Building an abstraction layer between internal services and external mobile or SaaS platform providers makes sense for a number of reasons from a strict security focused point of view, however there are also a number of benefits to utilizing this approach that may not be immediately apparent that can help to justify the adoption of these solutions.
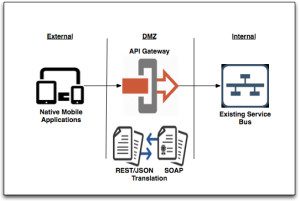
1) Rapid enablement of mobile and cloud services: Most organizations these days have already invested significantly in developing services that enable their business. It makes sense to leverage these existing services, but with the adoption of Mobile and Cloud based service requirements (such as REST, OAUTH, etc) the choice to re-tool can be a costly one. Products like Oracle API Gateway can be used to translate these types of requests into formats expected by your existing services catalog. This can significantly cut down the time required to enable access to these solutions from these new services.
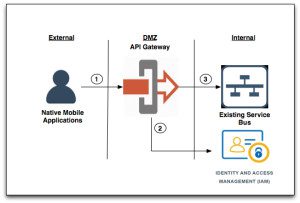
2) Abstraction of external identities integrated with existing services: Often times, existing services that are deployed within the organization were not initially envisioned to be consumed by users or entities outside of the organization. Many organizations, in order to leverage existing investments in development assets, want to do so but are concerned with the lack of security controls that may not have been built into existing services infrastructures. An API Gateway is an excellent place to implement such controls when introducing these services to new user constituencies. By integrating a new or existing Identity and Access Management infrastructure with your Gateway, you can introduce controls such as strong authentication, certificate requirements or even a security token services to protect access to these services while minimizing redevelopment of these assets.
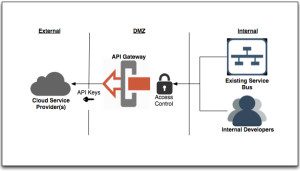
3) Centralization of Cloud Service API Key usage: The traditional approach to securing our organizations has been a perimeter focused exercise where the concern has been to protect the organization from external threats intruding into corporate networks. As mobile and clouds services blur the lines of our borders, it is important to consider those assets which may grant user access to information that may be stored within a cloud service provider. Many providers allow organizations to interact with their hosted data in a programatic fashion. Often, providers authenticate these types of request using ‘API Keys’ that are issued to customer organizations and users. One core tenant of a strong IAM posture is that no credential should ever be shared between two parties consuming the same service. This creates a management headache when dealing with externally hosted cloud service providers that issue such API ‘access keys’. Issuing individual keys to each developer may not only be impractical, but also represents certain security and operational management concerns. By routing internal requests to external service providers through a gateway, there is an opportunity to provide common access control based on a pre-exiting internal credential, certificate, etc. Once the request is authenticated and authorized, the API Key for the given service can be applied to the request at the gateway layer. In this way, management of such functionality is centralized and protected using trusted standards.
There are many obvious benefits to protecting service based requests coming into and going out of your organization’s infrastructure, but some are not quite as plain to see. Clearly, mobile and social technologies present great potential benefits, but come with a new set of risk. It is important to make sure we are leveraging all of the tools available to us in order to ensure these services are delivered with minimal risk of exposure to the enterprise.