Start With The End In Mind: Blog #7 – Lower the Cost of Compliance
 (Source: SailPoint Technologies, Inc. Identity and Access Management Buyers Guide)
(Source: SailPoint Technologies, Inc. Identity and Access Management Buyers Guide)
Compliance can be complex and difficult — and as a result, costly. Meeting industry and regulatory mandates requires organizations to regularly review and certify user access privileges. This leaves many companies constantly battling with error-prone and inefficient processes such as manually generating access reports and manually remediating inappropriate user access privileges. Signs that show you need to cut compliance costs include:
- Building or leveraging multiple, homegrown solutions to handle audit and compliance needs
- Hiring full-time staff or consultants to handle compliance projects like access certifications and SoD policy enforcement
- Using inefficient tools like spreadsheets and email to drive manual compliance processes
- Treating high-risk and low-risk users the same, where insufficient attention is given to high-risk users, or too much time and effort is spent on low-risk users.
To gain better control of your identity and access data, including centrally defining policy and risk and automating your access certification process, you need to replace expensive paper-based and manual processes with automated tools. By doing so, not only can you significantly reduce the cost of compliance, you can also establish repeatable practices for a more consistent, auditable, reliable and easier-to-manage access certification effort. If you struggle to effectively implement compliance processes and integrate them into your systems and infrastructure, a governance-based identity and access management solution is the launching pad you need to improve your effectiveness and reduce the costs of sustainable compliance.
Check back for blog #8, Salvage or Replace an Existing Provisioning System
Visit SailPoint Technologies, Inc. here.
Learn more about PathMaker Group IAM MAP here.

 (Source:
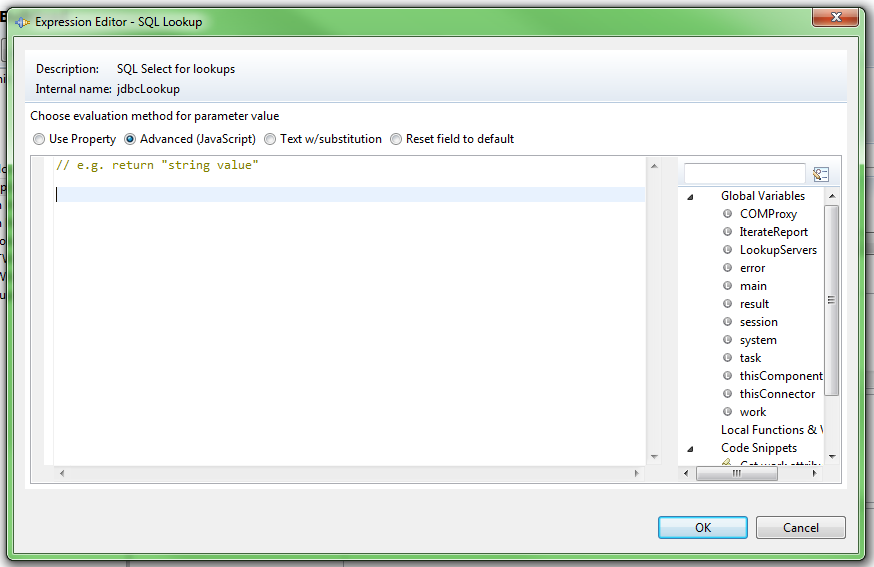
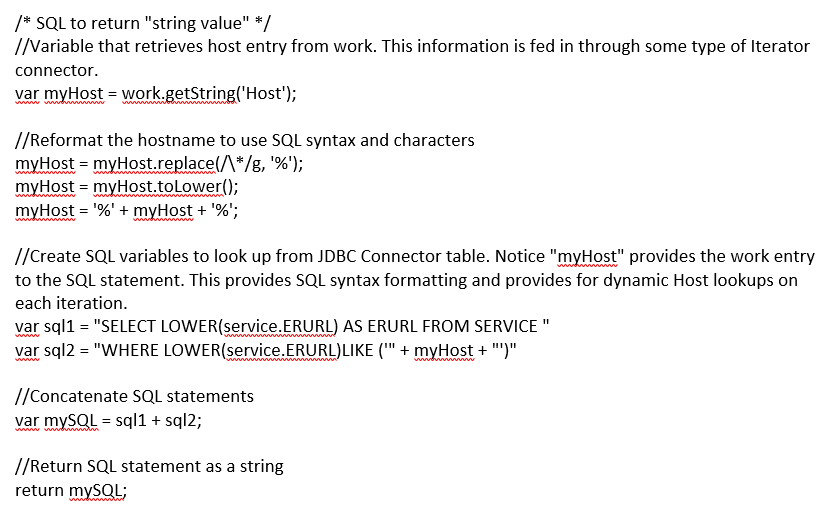
(Source:  Security Directory Integrator, formally known as Tivoli Directory Integrator, is a powerful tool that we often use to bulk load data into ISIM. Security Directory Integrator, otherwise known as SDI, has the capability of transforming data of one type to another. One of the challenges is querying specific data from a database source. For example, we often use a SDI to match existing system data to another source based on a User ID, Employee ID, or some type of unique identifier that is maintained in both systems.
Security Directory Integrator, formally known as Tivoli Directory Integrator, is a powerful tool that we often use to bulk load data into ISIM. Security Directory Integrator, otherwise known as SDI, has the capability of transforming data of one type to another. One of the challenges is querying specific data from a database source. For example, we often use a SDI to match existing system data to another source based on a User ID, Employee ID, or some type of unique identifier that is maintained in both systems.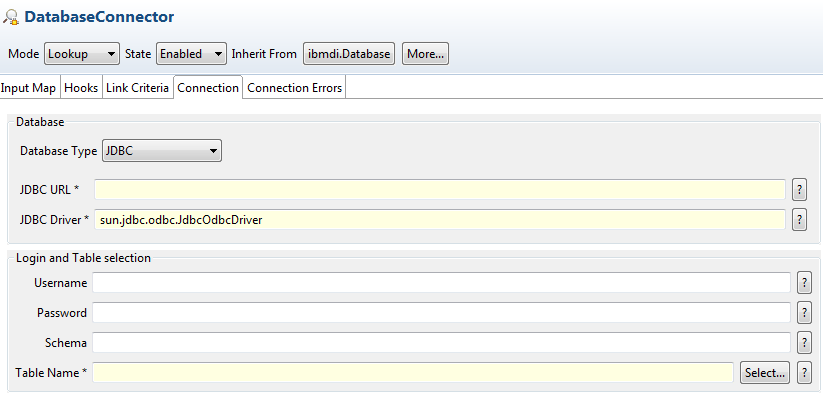
 (Source:
(Source: